Ransomware, server breakdowns, data leaks, health or geopolitical crises... IT crises cannot be prevented. But they can be anticipated. Yet few businesses are really prepared. And in a hurry, without tried and tested disaster recovery plans, runbooks If the roles are not clearly defined, chaos is guaranteed! So how do you prepare? How can you draw on ITSM, cyber best practice and experience in the field to avoid the worst: improvisation?

The facts are clear: there have never been so many IT crises in France.
According to the latest overview from ANSSI, the French national agency for information systems security, the number of security events rose by 15 % in 2024. This trend is reflected in incidents of impressive scale, as illustrated by the massive cyber attack on France Travail in early 2024, which exposed the personal data of 43 million people (and their social security numbers).
No one has been spared: public services (the city of Lille, hospitals in Brest and Cannes, etc.), as well as private giants (Free, SFR, Picard, Kiabi, Intersport, etc.), from the simple theft of data to the total paralysis of services.
And let's make no mistake about it, the impact is no longer just on IT. It can be industrial and systemic. The anecdote of Jaguar Land Rover at the end of 2025 is a real lesson: a cyber attack brought their British factories to a halt, freezing the global supply chain. The domino effect was so violent that the British government had to guarantee a €1.7 billion loan to save the company and its suppliers. The IT crisis of a single player became the crisis of an entire country's automotive ecosystem.
Faced with this reality, the question is: are you ready to manage a crisis?
Chronology of an IT crisis
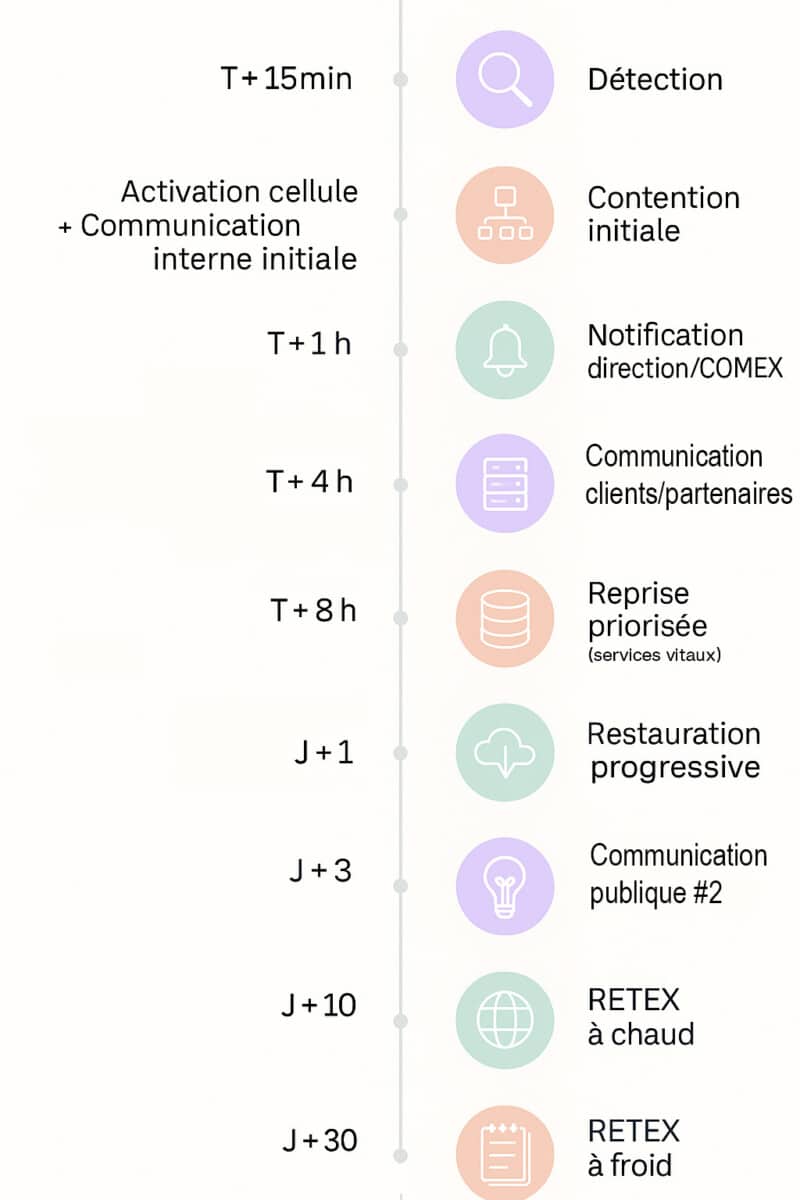
Stage 1 - Before the crisis: getting ready
If you can't always avoid a crisis, the best way to overcome it is to be prepared.
This preparation phase is not a constraint, it's your life insurance. The aim is simple: to minimise surprises on the big day.
This preparation enables the right tools to be put in place, roles to be clarified and training to be carried out. The more prepared an organisation is, the more the stress generated by the surprise effect is mitigated, enabling it to act methodically and effectively when the time comes.
5 actions to prepare
Five actions form the basis of any crisis resilience strategy:
- Define clear governance : not to play "Who's the boss?" in the middle of a storm. Formalise who takes the strategic decisions (the crisis unit) and who executes on the ground (the operational unit).
- Prepare continuity and recovery plans: the BCP aims to maintain essential activities in degraded mode during the crisis. For its part, the aim of the DRP is to restart information systems as quickly as possible after a disaster. These plans must be documented, known to everyone and, above all, tested regularly.
- Formulating a communication strategy : Who is speaking? To whom (employees, customers, etc.)? To say what? Preparing messages and channels in advance will prevent you from communicating in a panic, which is the best way to destroy trust.
- Contract for services and take out cyber insurance: nobody has all the skills in-house. Having an incident response company and cyber insurance under contract is like having the fire brigade's number before the fire breaks out.
- Train regularly: Crisis simulation is an often overlooked but crucial exercise. Whether it's a tabletop simulation ("tabletop exerciseWhether it's a training session (e.g. "how to use the new system") or a test in real-life conditions, this training helps to test the robustness of the procedures, identify sticking points and ensure that everyone knows their role.
ANSSI Council
Don't be content with PowerPoint presentations. ANSSI is adamant that full technical simulations (actual restoration of backups, switchover to the backup site) are the only ones that reveal the real problems. This is when you discover that the backup was not working or that the switchover procedure had not been updated for three years.
The crisis unit: who does what?
In an emergency situation, the usual hierarchy disappears. The golden rule is that the function takes precedence over the grade. The Crisis Unit (CDC) is an alternative form of governance, made up of a multi-disciplinary team (IT, management, communications, legal) whose sole aim is to steer the organisation through the storm.
It is structured on two levels:
- The strategic (or decision-making) unit : Comex, general management, legal affairs, communications and business representatives. Its role? Evaluate the impact, arbitrate on major decisions (whether or not to pay the ransom), validate communications and preserve reputation.
- Operational unit (cyber and IT): CIO, CISO, SOC and CSIRT experts. Their mission? Dive into the technical side to contain the attack, investigate and rebuild.
One of the first actions of the crisis unit will be to isolate the incident to prevent it spreading. This may involve taking certain servers offline, disconnecting them from the Internet or restoring healthy backups.
Crisis unit: roles and responsibilities
| Role | Primary responsibility | SKILLS |
|---|---|---|
| Manager (coordinator) | Steers decisions, arbitrates, maintains strategic direction | Leadership, composure, global vision, recognised authority |
| Spokesperson/communications | Manages external communications and is the public face of the organisation | Media skills, communications strategy, crisis management |
| Secretary | Ensures that all decisions, information and events can be traced (daily log) | Organisation, rigour, ability to summarise, monitoring tools |
| IS Coordinator (e.g. CIO, CISO) |
Provides targeted expertise to qualify the attack and guide the response | Knowledge of the field, ability to communicate in layman's terms |
Crisis communication
Crisis communication is an area that is often underestimated. Yet it is essential to quickly inform stakeholders (employees, customers, partners, regulatory authorities) of the situation and the measures taken. Transparent and regular communication helps to maintain trust and limit the impact on reputation. The example of the Intersport data leak demonstrated the importance of clear communication and precise recommendations to affected customers.
Le crisis secretaryamong other specific functions, plays an essential role in the maintenance of thea logbook (or handbook) of events, questions and decisions. This log is crucial not only for the traceability of actions, but also for the feedback (Retex). It is vital that reflex cards (or runbooks) of the crisis manager, the IS coordinator and the secretary are defined in advance and can be easily consulted.
The crisis unit is the "strategic heart of emergency management". Its composition must be clear and its roles defined in advance to guarantee rapid, coordinated decision-making.
Despite the best preparations, a crisis can still occur. Your responsiveness at this stage is crucial to triggering the right response.
Stage 2 - The start of the crisis: sounding the alarm
When a crisis occurs, the speed of response is crucial. The first step is to detect and qualify the incident as quickly as possible.
Is it a simple technical incident or a crisis situation that exceeds current management capabilities and requires exceptional mobilisation? Is it a hardware failure, a cyber attack or human error? Assessing the scale of the incident is crucial to the next stage of operations.
The critical threshold has been reached
The crisis unit is activated when a "critical threshold" is crossed. This is no longer an incident for which a procedure exists. This is an exceptional situation where the usual manual is no longer sufficient. This threshold is reached when three criteria are met:
- Gravity : the impact on business is major or expected to be major (e.g. production is halted).
- The emergency : Every minute that passes makes the situation worse.
- Potential impact : the long-term repercussions if nothing is done (e.g. the company's reputation is at stake).
Activating the crisis unit
Once the threshold has been reached, mobilisation must be immediate and follow a structured sequence. In a situation of maximum stress, these predefined steps are your safeguard against panic and improvisation.
- Alerting members : the pre-defined members of the crisis unit are contacted via reliable and rapid channels, prepared in advance (grouped SMS messages, dedicated collaborative tools, automated calls).
- Mobilising cells : the strategic and operational teams meet (physically or virtually) to establish an initial shared diagnosis.
- Apply the reflex cards (runbooks) : These checklists, prepared for each potential crisis scenario, detail step-by-step the procedures to be followed. They reduce stress and the risk of human error by providing a clear and precise framework for technical teams. They include critical actions, such as isolating compromised systems from the network or protecting healthy back-ups.
Once the cell has been activated and the first precautionary measures have been taken, crisis management takes place on two parallel fronts: technical and business.
Stage 3 - During the crisis: steering through the storm
Managing a crisis involves more than simply resolving the incident technically. It means fighting a war on two fronts: the technical battle to regain control of the IS and strategic battle to limit the impact on the business.
A dual strategy for global control
To manage the crisis effectively, the crisis unit relies on two complementary strategies that need to work together.
| Objective | CYBER RESOLUTION STRATEGY | BUSINESS CONTINUITY STRATEGY |
|---|---|---|
| 1 | Understanding the enemy: qualifying the attack, identifying the scope of the compromise. | Assessing and limiting the impact of malfunctions on critical processes. |
| 2 | Protect uncompromised IS and regain control of compromised IS. | Enabling a gradual resumption of activities, even in degraded mode, thanks to the BCP. |
Communicating to maintain trust
Poor communication can turn a technical crisis into a reputational crisis.
Communication is therefore essential to inform and reassure employees, but also to maintain the confidence of the external ecosystem (customers, partners, authorities, media).
For comprehensive crisis management, it is essential that communications work hand in hand with the technical response.
Effective crisis communication is based on three main principles:
- Transparency and facts : only communicate reliable and verified information. It is better to say "we are actively investigating" than to give false information or false promises.
- Adapting the message : the message must be adapted to its recipients. For example, employees should be given clear instructions on what tools are unavailable and what procedures to follow. For customers, the estimated recovery times should be communicated, without going into the technical details of the attack.
- Controlling time : Communicate on an ongoing basis to stay on top of things and not give in to media pressure or rumours. Prolonged silence can be interpreted as a loss of control.
Points to watch :
ANSSI insists on this point: in crisis communication, anyone who doesn't speak up is wrong. You have to take advantage of the media to keep control of the narrative.
5 questions / 5 answers survival kit
| Question | Type of crisis | Response |
|---|---|---|
| 1. What should you do as soon as you detect a compromised machine? | All types | Insulate immediately the machine or the network segment, but the keep lit to preserve technical evidence (logsmemory). |
| 2. When faced with a ransom demand, should you pay? | Cyber crisis (ransomware) | No, it is We strongly advise against paying. Focus on technical resilience and recovery from healthy backups. |
| 3. If the IS is totally unusable, what is the priority? | Major IT crisis (unavailability) | Activate the business continuity plan (BCP) and resilient rescue tools (offline directories, alternative communications). |
| 4. What should I do if my personal data is stolen or leaked? | Cyber crisis (data theft) | File a complaint and proceed with the regulatory declaration mandatory, in particular with the CNIL (RGPD). |
| 5. Who has priority for communication in the acute phase? | All types (communication) | The teams and staff must be informed quickly to avoid rumours and ensure a coherent response. |
The crisis is now under control. It's time to organise the way out of the crisis and, above all, to capitalise on this ordeal.
Stage 4 - After the crisis: capitalising on experience
The storm has passed. But the work has only just begun. The end of a crisis is not simply a return to normality. It's the start of an essential phase of reconstruction, analysis and continuous improvement. The aim is to emerge from the ordeal not weakened, but strengthened.
Feedback (Retex)
Once the crisis has been resolved, it is essential to carry out a post-experience review. The aim of this "post-mortem" examination is to analyse how events unfolded, and to identify strengths and areas for improvement.
It's not about finding the culprits, but about understanding what has worked and what needs to be improved.
The analysis should focus on concrete aspects such as the quality of information exchanges, the operation of equipment and materials as well as the relevance of decision-making.
The Retex takes place in two stages:
- Hot off the press: Immediately after the crisis is over, an initial meeting is held to gather impressions and highlights while memories are still fresh.
- Cold : A few weeks later, a more in-depth and dispassionate analysis enables a concrete action plan to be drawn up to improve processes, tools and training.
The opportunity to grow stronger
Every crisis is a brutal but incredibly effective lesson. It exposes your weaknesses in a way that no audit ever could. It's a unique opportunity to justify budgets, harden your systems and reinforce the security culture across the business. Resilience isn't a state, it's a muscle that gets stronger with every test.
In conclusion, while there is no such thing as zero risk, rigorous preparation and structured crisis management can minimise the impact of an IT incident. In the face of constantly evolving threats, anticipation and training remain the best weapons. The French government is offering the following training courses SenCy-Crise Cybermalveillance.gouv.fr, while ORSYS offers a range of programmes to anticipate and manage crises. Because on D-day, it's best to be ready !




